How Does a Hash Help Secure Blockchain Technology? As we go on a quest to comprehend the deep workings of blockchain technology, we must cast a light on a quiet but mighty guardian: the hash function. This essay tries to demystify the critical role that hash functions play in ensuring the integrity and immutability of blockchain technology, offering a solid foundation for newcomers navigating the intriguing world of decentralised ledgers.
Hash Functions 101: Creating Digital Fingerprints
To understand the power of hash functions, let us first define their fundamental notion. Consider a hash function to be a digital fingerprint generator that assigns a unique alphanumeric string, known as a hash, to each piece of data it processes. These digital fingerprints serve as the foundation of blockchain, guaranteeing that data stored is tamper-proof and resistant to change.
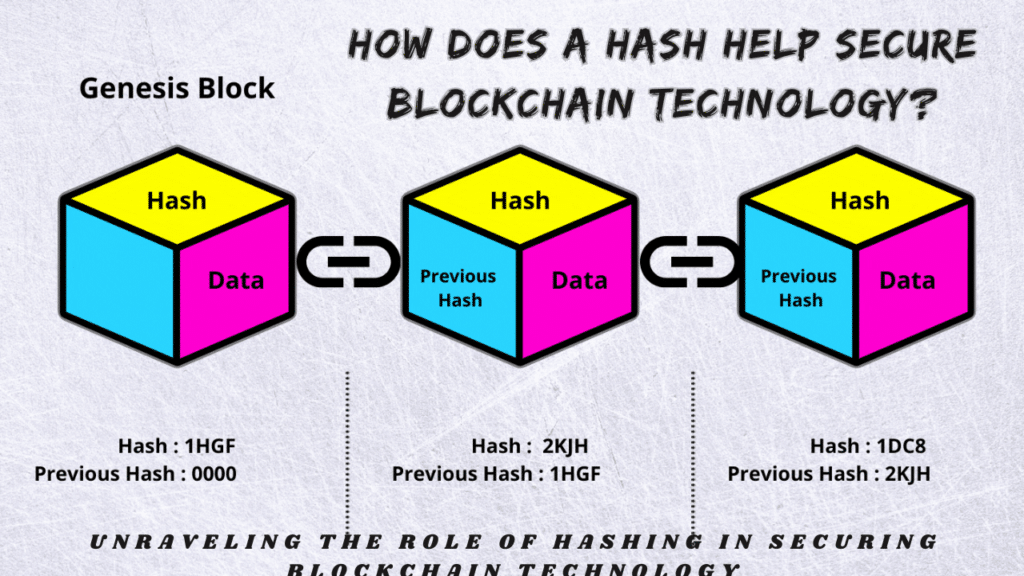
The pillars of blockchain security: immutability and integrity
-
Immutability: A Cryptographic Puzzle Revealed:
Immutability is fundamental to blockchain security. Consider the blockchain to be a series of linked blocks, each storing the previous block’s hash. This generates a cryptographic puzzle. Any attempt to update the information in a block changes its hash and breaks the succeeding block’s reference to it. Tampering becomes a severe obstacle since it involves changing every subsequent block in the chain, which is a difficult undertaking considering the computer resources needed.
-
Ensuring Data Integrity: The Unbreakable Chain of Trust:
Consider a digital book in which each page references the preceding page’s material before concluding with its own summary. Changing a single page alters its hash, causing a cascade impact across the book. Hash functions on the blockchain maintain data integrity. Any update to a block’s contents changes its hash, sending an obvious signal to the network that foul play is taking place.
The Miner’s Role: Create Digital Seals of Approval
Within the blockchain ecosystem, miners play the function of digital blacksmith. They compete to solve complex mathematical riddles, with the first to succeed receiving the privilege of adding the next brick to the chain. The miner’s hash becomes the official mark of approval for the new block, demonstrating the shared effort to ensure the blockchain’s security and integrity.
Protecting Against Malicious Intent: The Strength of Cryptographic Security
Hash functions are secure because of their cryptographic features. Even little changes to the input data result in an altogether new hash, and the one-way nature of this process makes it very difficult to reverse-engineer the original data. Cryptographic hash algorithms, such as the commonly used SHA-256, are specifically engineered to resist assaults, strengthening the blockchain’s defences against malevolent intent.
Conclusion: Hash Functions—The Unsung Heroes of Blockchain Security
In the rich fabric of blockchain technology, hash functions emerge as unspoken Heroes are quiet but strong guards that ensure the trustworthiness of the decentralized ecosystem. As newcomers traverse the digital vastness of blockchain, understanding the role of hash functions is critical. These digital fingerprints protect data and form the cornerstone of a system that offers openness, security, and decentralisation.
Also Read: Fashion Institute of Technology
To summarise, for those travelling into the enthralling realm of blockchain, let the hash function be your guiding light—a quiet sentinel maintaining the purity of each block and reinforcing the blockchain against the winds of meddling and deception. These are all the answers to How Does a Hash Help Secure Blockchain Technology?